New analysis from cybersecurity firm Volexity particulars a extremely refined assault deployed by a Chinese language-speaking cyberespionage risk actor named StormBamboo.
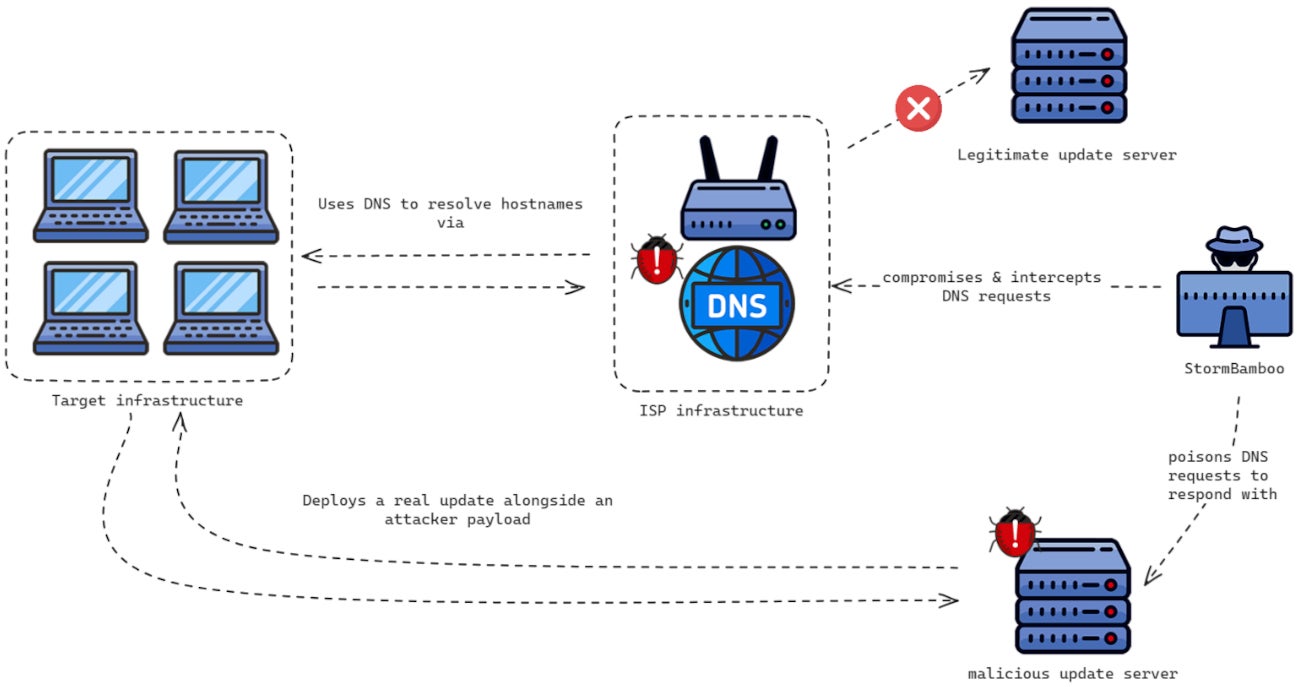
The risk actor compromised an ISP to alter some DNS responses to queries from techniques requesting reputable software program updates. A number of software program distributors had been focused. The altered responses resulted in malicious payloads served by StormBamboo along with the reputable replace information. The payloads focused each macOS and Microsoft Home windows working techniques.
Who’s StormBamboo?
StormBamboo – also referred to as Evasive Panda, Daggerfly, or Bronze Highland – is a China-related cyberespionage risk actor, lively since at the least 2012. The Chinese language-speaking group has focused many organizations aligned with Chinese language pursuits worldwide.
Through the years, the group has focused people in mainland China, Hong Kong, Macao and Nigeria. As well as, it focused entities, together with governments, in Southeast Asia, East Asia, the US, India and Australia.
The group has an extended historical past of compromising reputable infrastructure to contaminate their targets with customized malware developed for Microsoft Home windows and macOS working techniques. The group deployed watering gap assaultswhich consists of compromising a particular web site to focus on its guests and infect them with malware.
StormBamboo can be able to conducting provide chain assaults, akin to compromising a software program platform, to discreetly infect individuals with malware.
The group can be in a position to goal Android customers.
ISP compromised, DNS responses poisoned
The risk actor managed to compromise a goal’s ISP infrastructure to manage the DNS responses of that ISP’s DNS servers – principally consisting of translating domains to IP addresses, directing them to the right web site. An attacker controlling the server could cause the computer systems to request a particular area title to an attacker-controlled IP tackle. That is precisely what StormBamboo did.
Whereas it isn’t identified how the group compromised the ISP, Volexity reported that the ISP rebooted and took a number of elements of its community offline, instantly halting the DNA poisoning operation.
The attacker aimed to alter DNS responses for a number of reputable utility replace websites.
SEE: Why Your Enterprise Ought to Think about Implementing DNS Safety Extensions
Paul Rascagneres, risk researcher at Volexity and an creator of the publication, advised TechRepublic in a written interview that the corporate doesn’t know precisely how the risk actors selected the ISP.
“The attackers in all probability did some analysis or reconnaissance to establish the sufferer’s ISP,” he wrote. “We do not know if different ISPs have been compromised; it’s difficult to establish it from the surface. StormBamboo is an aggressive risk actor. If this working mode was successful for them, they may apply it to different ISPs for different targets.”
Official replace mechanisms are being abused
A number of software program distributors had been focused by this assault.
As soon as a consumer DNS request was despatched to the compromised DNS server, it responded with an attacker-controlled IP tackle that delivered an precise replace for the software program—however with an attacker’s payload.
The Volexity report confirmed that a number of software program distributors utilizing insecure replace workflows had been involved and offered an instance with a software program known as 5K participant.
The software program checks for updates for “YoutubeDL” each time it’s began. The checking is completed by requesting a configuration file, which signifies whether or not a brand new model is offered. If that’s the case, it’s downloaded from a particular URL and executed by the reputable utility.
Nonetheless, the compromised ISP’s DNS will direct the app to a modified configuration file, indicating there may be an replace, however delivering a backdoored YoutubeDL package deal.
The malicious payload is a PNG file containing both MACMA or POCOSTICK/MGBot malware, relying on the working system requesting the replace. MACMA infects MacOS, whereas POCOSTICK/MGBot infects Microsoft Home windows working techniques.
Malicious payloads
POCOSTICK, also referred to as MGBot, is a customized malware probably developed by StormBamboo because it has not been utilized by some other group, based on ESET. The malware has been round since 2012 and consists of assorted modules that allow keylogging, file theft, clipboard interception, audio stream seize, cookie and credential theft.
Conversely, MACMA permits keylogging, fingerprinting of sufferer gadgets, and display and audio recording. It additionally supplies a command line to the attacker and has file stealing capabilities. Google initially reported the presence of MACMA malware in 2021 utilizing watering gap assaults to deploy.
The Google assault was not attributed to a risk actor, but it surely focused guests from Hong Kong web sites for a media outlet and a distinguished pro-democracy labor and political group, based on Google. This assault aligns with StormBamboo’s goal.
Volexity additionally discovered important code similarities between the newest MACMA model and one other malware household, GIMMICK, which was launched by the storm cloud risk actor.
Lastly, in a single case after compromising a sufferer’s macOS gadget, Volexity noticed the attacker deploy a malicious Google Chrome extension. The obfuscated code permits the attacker to exfiltrate the browser’s cookies to an attacker-controlled Google Drive account.
How can software program suppliers defend customers from cyber threats?
Rascagneres advised TechRepublic that Volexity recognized a number of focused insecure replace mechanisms from totally different software program: 5k Participant, Fast Heal, Sogou, Rainmeter, Partition Wizard and Corel.
Requested methods to defend and enhance the replace mechanisms on the degree of software program suppliers, the researcher insists that “the software program editors ought to implement HTTPS replace mechanism and examine the SSL certificates of the web site the place the updates are downloaded. Moreover, they have to signal the updates and confirm this signature earlier than executing them.”
With the intention to assist firms detect StormBamboo exercise on their techniques, Volexity supplies YARA guidelines to detect the varied payloads and recommends blocking the indications of the corporate’s compromise provide.
Disclosure: I work for Development Micro, however the opinions expressed on this article are my very own.
========================
AI, IT SOLUTIONS TECHTOKAI.NET
