Software program Highlight: CrowdStrikeCrowdStrike Falcon® Cloud Safety is a unified cloud safety platform that protects infrastructure, purposes, knowledge, AI, and SaaS throughout hybrid and multi-cloud environments. It allows organizations to consolidate instruments, scale back complexity, and cease breaches.
|
Cloud safety posture administration, or CSPM instruments, are automated safety options designed to repeatedly monitor and assess cloud infrastructures, companies, and purposes for misconfigurations and compliance points.
These instruments are extra necessary than ever as extra organizations now leverage the multicloud method to cloud adoption, a follow that comes with configuration and safety compliance complexities. In accordance with a Fortinet-sponsored report performed by cybersecurity consultants, many organizations are actually more and more cautious of AI-based threats, prompting them to have heightened concern about cloud safety.
To handle this problem, many cloud-first organizations now deploy CSPM instruments to assist them monitor, determine, alert, and remediate compliance dangers and misconfigurations of their cloud environments.
To find out which CSPM device is finest suited on your group, I’ve compiled a listing of the highest CSPM options for 2024.
Semperis
Workers per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Massive (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Massive, Enterprise
Options
Superior Assaults Detection, Superior Automation, Wherever Restoration, and extra
Uniqkey – Enterprise Password Supervisor
Workers per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Small (50-249 Workers), Medium (250-999 Workers), Massive (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Small, Medium, Massive, Enterprise
Options
Exercise Monitoring, Dashboard, Notifications, and extra
What’s cloud safety posture administration?
CSPM instruments will help customers preserve a safe cloud posture by recommending finest practices and imposing safety insurance policies throughout all cloud accounts and companies. These insurance policies can embrace entry controls, encryption settings, community configurations, and extra. By automating the enforcement course of, CSPM software program minimizes the chance of misconfigurations and helps defend in opposition to threats or exterior assaults.
SEE: Brute Pressure and Dictionary Assaults: A Information for IT Leaders (TechRepublic Premium)
Greatest cloud safety posture administration software program comparability
The desk beneath gives a comparability of key options accessible in every CSPM choice.
Greatest cloud safety posture administration software program
Here’s a rundown of the seven finest CSPM software program selections in 2024, highlighting their options, pricing plans, professionals, and cons.
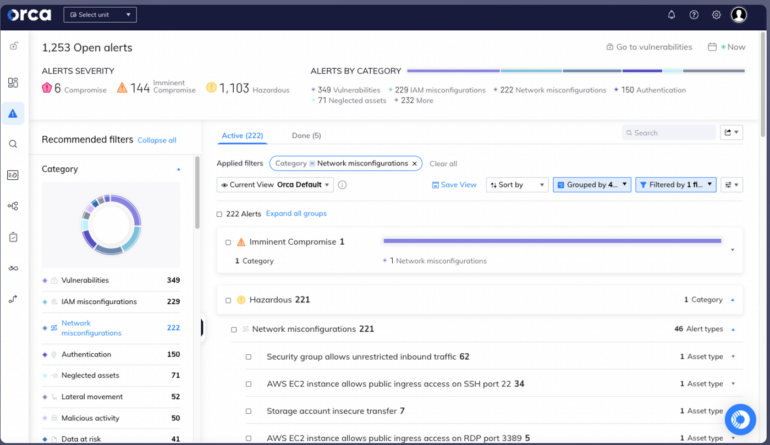
Orca Safety: Greatest for cloud workloads

Orca presents customers with a CSPM device that scans their workloads and maps the outcomes right into a centralized platform. It could analyze dangers and determine conditions the place seemingly unrelated points might result in dangerous assault paths. With these insights, Orca prioritizes dangers, minimizing the burden of extreme alerts for customers.
SEE: Every little thing You Must Know in regards to the Malvertising Cybersecurity Risk (TechRepublic Premium)
Orca additionally facilitates steady monitoring for cloud assaults. It incorporates a visible graph to provide perception into a company’s potential assault floor and the attacker’s finish goal inside a cloud setting.
Relating to compliance, Orca gives compliance options that allow cloud sources to stick to regulatory frameworks and {industry} benchmarks, together with knowledge privateness necessities. The platform unifies compliance monitoring for cloud infrastructure workloads, containers, identities, knowledge, and extra, all inside a single dashboard.
Why I selected Orca Safety
I’ve Orca Safety on this checklist as a result of it’s a high quality resolution for organizations that primarily work on the cloud. Its threat evaluation and identification of cloud workloads make it a useful gizmo to fight unnoticed threats. For my part, its intensive reporting and insights performance, protecting a company’s assault floor, is one other function inclusion that makes it a best choice for these trying to handle vulnerabilities or forestall future assaults.
Pricing
Orca presents a 30-day free trial. Contact Orca to get a quote.
Options
- Cloud compliance.
- Unified Knowledge Mannequin.
- Steady monitoring.
- Orca Safety Rating.
- Assault path evaluation.
- PII detection.
- Malware detection.
Orca Safety professionals and cons
| Professionals | Cons |
|---|---|
| Customers can create personalised views of Orca’s Danger Dashboard. | No pricing data is on the market on its web site. |
| This resolution presents a 30-day free trial. | |
| It helps organizations meet compliance with PCI-DSS, GDPR, HIPAA, and CCPA. | |
| Customers can generate complete cloud safety studies and share them throughout numerous channels. | |
| Customers can write their very own alert queries or use over 1,300 prebuilt system queries. |
Prisma Cloud: Greatest for multicloud environments

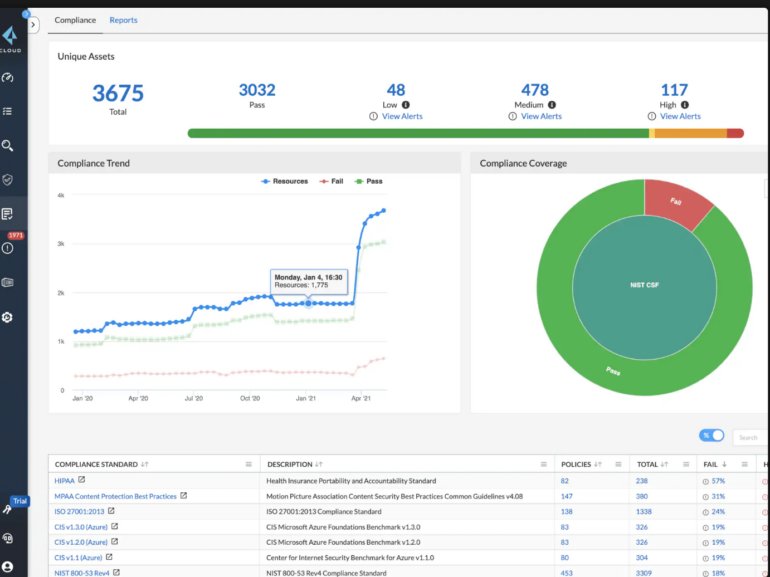
Prisma Cloud by Palo Alto Networks presents complete visibility and management over the safety posture of deployed sources in multicloud environments. The answer will help customers implement prompt configurations with over 700 pre-defined insurance policies from greater than 120 cloud companies. That function can support organizations in correcting typical multicloud misconfigurations, stopping potential safety breaches, and creating customized safety insurance policies. With Prisma Cloud, customers may also profit from steady compliance posture monitoring and one-click reporting, providing protection for numerous laws and requirements, together with CIS, GDPR, HIPAA, ISO-27001, NIST-800, PCI-DSS, and SOC 2. The answer additionally gives customized reporting.
SEE: What’s Cloud Safety? Basic Information (TechRepublic)
Prisma Cloud presents community menace detection and consumer entity habits analytics options, permitting prospects to determine uncommon community actions, DNS-based threats, and insider threats by monitoring billions of movement logs acquired each week.
Why I selected Prisma Cloud
I chosen Prisma Cloud resulting from it being a top quality choice for organizations already using multicloud environments. With an increasing number of firms adopting multicloud, I notably respect Prima Cloud’s pre-defined insurance policies and built-in community menace detection. These will help catch holes or threat areas throughout a number of cloud suppliers.
That is particularly essential with multicloud environments, as totally different cloud suppliers might not have seamless integration with each other and thus want extra monitoring for safety vulnerabilities.
Pricing
Contact Prisma Cloud for a quote.
Options
- Community menace detection.
- Consumer entity habits analytics.
- Knowledge safety.
- Compliance reporting.
- Configuration evaluation.
- Automated remediation.
- Multi-cloud knowledge visibility.
Prisma Cloud professionals and cons
| Professionals | Cons |
|---|---|
| Helps safety and compliance administration. | No pricing data on its web site. |
| Gives knowledge governance with customizable insurance policies. | |
| Built-in menace detection dashboards. | |
| Consists of malware detection capabilities. | |
| Has a menace alert system. |
Wiz: Greatest for managing identity-based publicity

Wiz is a CSPM device designed to repeatedly detect and remediate misconfigurations throughout notable clouds, together with AWS, GCP, Azure, OCI, Alibaba Cloud, and VMware vSphere. By establishing connections to customers’ cloud environments, Wiz delivers complete visibility and actionable context on customers’ vital misconfigurations, enabling groups to reinforce their cloud safety posture. The answer additionally presents community and identification publicity, which facilitates the identification of uncovered sources by way of its graph-based community and identification engine.
SEE: Cybersecurity and Cyberwar (TechRepublic on Flipboard)
With its automated posture administration and remediation function, customers can mechanically assess over 1,400 configuration guidelines throughout totally different cloud runtimes and infrastructure-as-code (IaC) frameworks. Moreover, customers may also construct customized guidelines utilizing the OPA (Rego) engine. Moreover, Wiz repeatedly assesses customers’ compliance posture in opposition to greater than 100 built-in compliance frameworks. It additionally permits customers to outline customized compliance baselines and frameworks, providing flexibility and customization choices.
Why I selected Wiz
I picked Wiz for its deal with identity-based safety, specifically for its identification misconfiguration and customized guidelines performance. This gives further safety for each excessive and low-profile customers, guaranteeing utmost safety regardless of the place you might be in your organization’s organizational chart. I additionally favored Wiz’s emphasis on identity-based publicity, as this helps forestall unauthorized entry to delicate firm sources when there are misconfigured permissions inside a system.
Pricing
Contact Wiz for a quote.
Options
- Assault path evaluation.
- Compliance reporting.
- Automated posture administration and remediation.
- Greater than 100 built-in compliance frameworks.
- Helps customized organizational compliance baseline.
Wiz professionals and cons
| Professionals | Cons |
|---|---|
| Community and identification misconfigurations are prioritized, specializing in vital areas. | No pricing data on its web site. |
| It permits customers to outline their very own organizational compliance baseline. | |
| Groups can simply detect misconfigurations that pose the best menace. | |
| It presents built-in guidelines and automation. |
PingSafe: Greatest for real-time cloud infrastructure monitoring

PingSafe mechanically assesses over 1,400 configuration guidelines that detect cloud misconfigurations. It has options that enable organizations to create customized insurance policies aligned with their distinctive safety necessities, safeguarding delicate knowledge and sources in opposition to potential threats. The software program additionally presents menace detection and remediation options to allow customers to observe the safety posture of their cloud infrastructure and see potential remediation steps. There’s additionally a context-aware alert system, which gives customers with notifications when misconfigurations happen. With real-time steady monitoring functionality, the software program will help safety groups remove blind spots throughout their cloud environments.
Why I selected PingSafe
I selected PingSafe for organizations that need a fixed monitoring device of their cloud setting. I envision PingSafe’s steady monitoring as a standout function for IT departments which are proactively on the lookout for weaknesses of their group’s system.
That is particularly helpful for bigger organizations given their complicated construction, presumably making them extra prone to wide-scale knowledge breaches or exploits.
Pricing
Contact PingSafe for a quote.
Options
- Context-aware alerts.
- Constructed-in guidelines.
- Actual-time detection and remediation.
- Customized question help.
- Asset discovery and real-time monitoring.
PingSafe professionals and cons
| Professionals | Cons |
|---|---|
| The agentless onboarding course of eliminates cloud prices and reduces agent vulnerabilities related to the agent-based method. | No pricing data on its web site. |
| Steady scanning of cloud belongings gives customers with a complete view of potential vulnerabilities and threats. | |
| Organizations can tailor insurance policies to their particular wants. | |
| Context-aware alerts present customers with actionable insights, permitting them to shortly handle misconfigurations. |
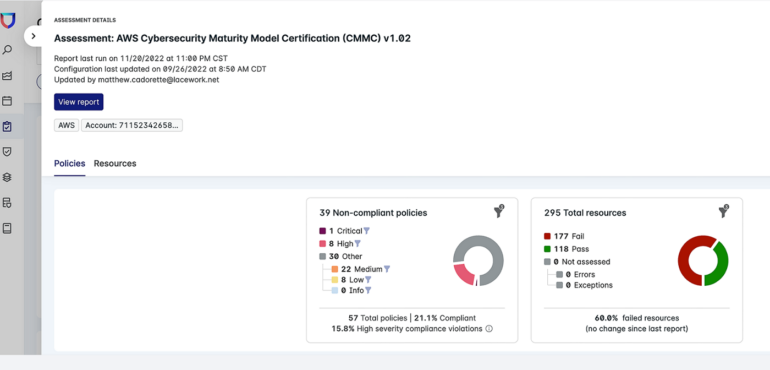
Lacework Polygraph Knowledge Platform: Greatest for stock administration and compliance

Lacework Polygraph Knowledge Platform permits for environment friendly stock administration of belongings throughout customers’ cloud environments. It retains observe of every day stock modifications, even for belongings that not exist, guaranteeing an up-to-date understanding of the cloud infrastructure. With a unified platform for AWS, Azure, Google Cloud, and Kubernetes configurations, Lacework presents customers a consolidated view of their compliance throughout cloud suppliers.
As a CSPM, Lacework additionally gives automated monitoring and detection of misconfigurations and suspicious cloud actions. As well as, Lacework permits customers to evaluate their posture and compliance in opposition to a number of pre-built insurance policies, together with PCI, HIPAA, NIST, ISO 27001, and SOC 2. Customers may also set customized insurance policies throughout cloud suppliers to fulfill their organizational necessities.
Why I selected Lacework Polygraph Knowledge Platform
I chosen Lacework for its helpful stock administration of a company’s cloud belongings. To me, that is vital for organizations that work totally on the cloud, because it removes the legwork of recording and managing these belongings and organizes them in a extra environment friendly and automatic method.
This additionally permits members of a company to deal with their priorities and firm objectives with out sacrificing total safety of their cloud environments.
Pricing
Contact Lacework for a quote.
Options
- Pre-built and customized insurance policies.
- Assault path evaluation.
- Risk detection.
- Push button studies.
Lacework professionals and cons
| Professionals | Cons |
|---|---|
| Customers can set customized insurance policies throughout cloud suppliers. | No pricing data on its web site. |
| With push-button studies, customers can shortly reveal their safety posture and compliance to prospects, companions and auditors. | |
| Customers can create customized studies in a number of codecs. | |
| It permits seamless integration with instruments like Jira and Slack. |
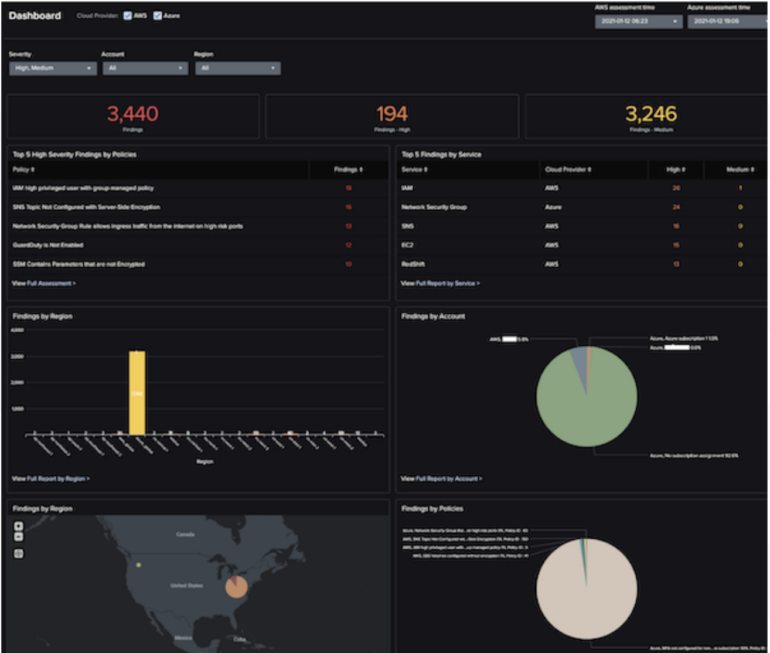
CrowdStrike Falcon Cloud Safety: Greatest for adversary-focused menace intelligence

One other CSPM device to think about is Crowdstrike Falcon Cloud Safety. It presents agentless monitoring of cloud sources to detect misconfigurations, vulnerabilities, and safety threats. It adopts an adversary-focused method, equipping customers with real-time menace intelligence on over 230+ adversary teams and 50 indicators of assault.
This platform additionally gives multicloud visibility, steady monitoring, menace detection and prevention capabilities whereas imposing safety posture and compliance throughout AWS, Azure, and Google Cloud. As well as, Crowdstrike Falcon Cloud Safety presents indicators of cloud infrastructure misconfigurations.
Why I selected CrowdStrike Falcon Cloud Safety
CrowdStrike Falcon marked its title on my checklist for its prioritization of adversary-focused threats. For organizations which are particularly involved with assaults, Falcon Cloud Safety’s database of adversary teams gives reassurance that your chosen CSPM device is proactive in its safety. I personally respect CrowdStrike’s efforts to repeatedly develop its checklist of adversary teams, particularly within the face of AI-based threats and know-how.
Pricing
Crowdstrike presents 4 pricing choices with a 15-day free trial:
- Falcon Go: Begins at $4.99 per machine, per 30 days.
- Falcon Professional: Begins at $99.99 per machine, per yr.
- Falcon Enterprise: $184.99 per machine, per yr.
- Falcon Elite: Contact gross sales for pricing.
Options
- Steady compliance monitoring.
- DevSecOps integration.
- Agentless monitoring.
- Actual-time menace intelligence.
CrowdStrike professionals and cons
| Professionals | Cons |
|---|---|
| Simplified administration and safety coverage enforcement. | Interface could also be complicated for some customers. |
| Gives guided remediation. | |
| Gives unified visibility throughout hybrid and multicloud environments. | |
| Gives real-time menace intelligence on adversary teams and indicators of assaults. | |
| Integrates with safety data and occasion administration options. |
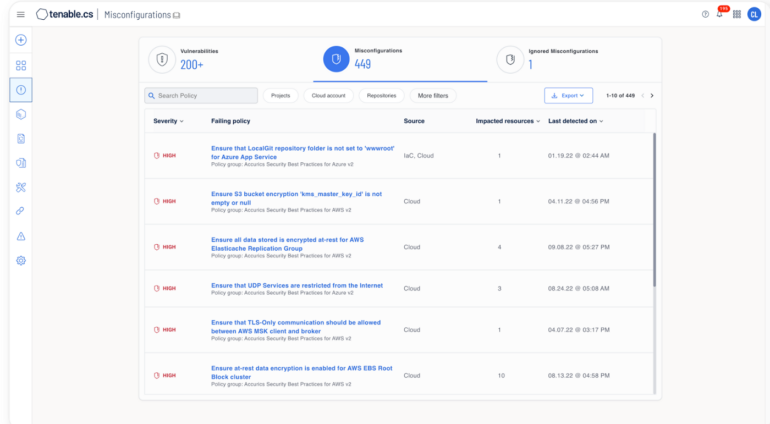
Tenable Cloud Safety: Greatest for dev and manufacturing environments

Tenable Cloud Safety gives its customers with a framework for imposing insurance policies throughout multicloud environments. Providing a number of pre-developed insurance policies, it permits customers to use {industry} benchmarks like these from the Middle for Web Safety and different requirements or create customized insurance policies. With Tenable, safety groups can scan their cloud setting to determine misconfigurations underneath a unified dashboard.
As a CSPM device, Tenable presents options which may curiosity customers resembling an automatic workflow that aids collaboration between DevOps and safety groups, automated compliance standing reporting, cloud stock visibility, and the capability to prioritize dangers based mostly on their stage of severity.
Why I selected Tenable Cloud Safety
I chosen Tenable Cloud Safety as a potential resolution for developer and manufacturing groups that need strengthened safety for his or her cloud infrastructure. Of its options, I discovered Tenable’s automated workflow to be particularly efficient in embedding safety into the event pipeline. This might assist detecting and remediating dangers, whereas permitting builders to make changes when essential.
Pricing
Contact Tenable for a quote.
Options
- Unified framework.
- DevOps integration.
- Configuration drift monitoring.
- Auto-remediation.
Tenable Cloud Safety professionals and cons
| Professionals | Cons |
|---|---|
| This resolution makes it straightforward to detect high-risk configurations that might result in breaches. | No pricing data on its web site. |
| Customers can simply implement and report compliance with pre-packaged governance profiles. | |
| It presents risk-based scoring to find out menace severity. | |
| It facilitates collaboration between DevOps and safety groups by way of automated workflows. | |
| Free trial is on the market. |
Key options of cloud safety posture administration software program
The next options are generally present in each top-quality CSPM software program choice.
CSPM instruments assist customers preserve a safe cloud posture by recommending finest practices and imposing safety insurance policies throughout all cloud accounts and companies. These insurance policies can embrace entry controls, encryption settings, community configurations, and extra. By automating the enforcement course of, CSPM software program minimizes the chance of misconfigurations and unintended publicity of delicate knowledge.
Compliance monitoring and reporting
Compliance with numerous requirements and laws is a high precedence for any cloud-first group. CSPM options facilitate compliance monitoring by recurrently auditing cloud environments in opposition to industry-specific requirements resembling PCI DSS, HIPAA, GDPR, SOC 2, and extra. These instruments generate complete studies and dashboards that assist organizations perceive their compliance standing, determine gaps, and take essential actions to fulfill regulatory necessities.
Cloud asset stock and visibility
Sustaining an correct stock of cloud belongings is crucial for efficient safety posture administration. CSPM instruments present visibility into a company’s cloud infrastructure, together with digital machines, storage accounts, databases, and different sources.
Actual-time cloud infrastructure monitoring
CSPM software program gives steady real-time monitoring of cloud customers’ infrastructure. This enables organizations to promptly detect potential safety threats and vulnerabilities, enabling them to reply shortly and mitigate dangers successfully.
How to decide on one of the best cloud safety posture administration software program for your small business
Choosing the appropriate CSPM software program is a vital resolution that impacts the safety and compliance of your cloud infrastructure. To make an knowledgeable alternative, contemplate the next steps:
Assess your group’s cloud posture administration wants
Earlier than going with any of the CSPM options, conduct an in-depth evaluation of your group’s cloud safety necessities. Determine the particular challenges, compliance requirements, and cloud suppliers you’re employed with to discover a resolution that finest aligns along with your goals.
Consider key options
Consider every software program based mostly on its means to fulfill your group’s wants. Prioritize options that instantly handle your safety considerations and streamline your cloud safety administration course of.
Contemplate scalability
Be certain that the CSPM software program you select is scalable and might accommodate the increasing calls for of your cloud setting.
Contemplate ease of use
Consumer-friendliness is necessary as your IT group will probably be working with the CSPM software program recurrently. A simple and intuitive interface can improve productiveness and make it simpler for organizations to navigate and implement safety measures successfully.
Request demos and trials
Earlier than making a closing resolution, you would possibly need to get a grasp of the product utilizing its demo or trial model. Happily, variety of CSPM device suppliers provide entry to free trials with no further value.
Methodology
To find out one of the best CSPM device accessible in 2024, I first performed an in-depth evaluation of the related suppliers, figuring out the main CSPM options out there at present. Subsequent, I assessed every software program’s options, compliance capabilities, and total scalability to ensure they align with numerous organizational wants. I additionally analyzed buyer suggestions and opinions from Gartner Peer Insights to raised perceive consumer experiences and the effectiveness of every resolution.
========================
AI, IT SOLUTIONS TECHTOKAI.NET
