Risk actors love phishing as a result of it really works. That is particularly efficient in cloud infrastructure – as soon as they’re inside, they’ve entry to the rest related to the cloud. In line with HornetSecurity’s cyber safety report 2025Greater than 471 million e -mails had been despatched in 2024 that had been labeled as ‘malicious’.
By way of electronic mail assaults, Phishing remained the highest assault technique at 33.3%. This makes it by far the most typical assault vector, subsequent to malicious URLs. However not all phishing is similar. Many focused phishing campaigns in opposition to particular people or kinds of people are generally known as Spiesphishing.
You will need to be capable to see phishing usually. However for Spiesphishing targets, it’s much more important to see the clear indicators, because the harm performed in these assaults is bigger.
Semperist
Staff per firm measurement
Micro (0-49), small (50-249), medium (250-999), giant (1 000-4,999), enterprise (5,000+)
Small (50-249 workers), medium (250-999 workers), giant (1,000-4,999 workers), enterprise (5,000+ workers)
Small, medium, giant, enterprise
Capabilities
Superior assaults detection, superior automation, wherever restoration, and extra
Uniqkey – Enterprise Password Supervisor
Staff per firm measurement
Micro (0-49), small (50-249), medium (250-999), giant (1 000-4,999), enterprise (5,000+)
Small (50-249 workers), medium (250-999 workers), giant (1,000-4,999 workers), enterprise (5,000+ workers)
Small, medium, giant, enterprise
Capabilities
Exercise monitoring, dashboard, notifications, and extra
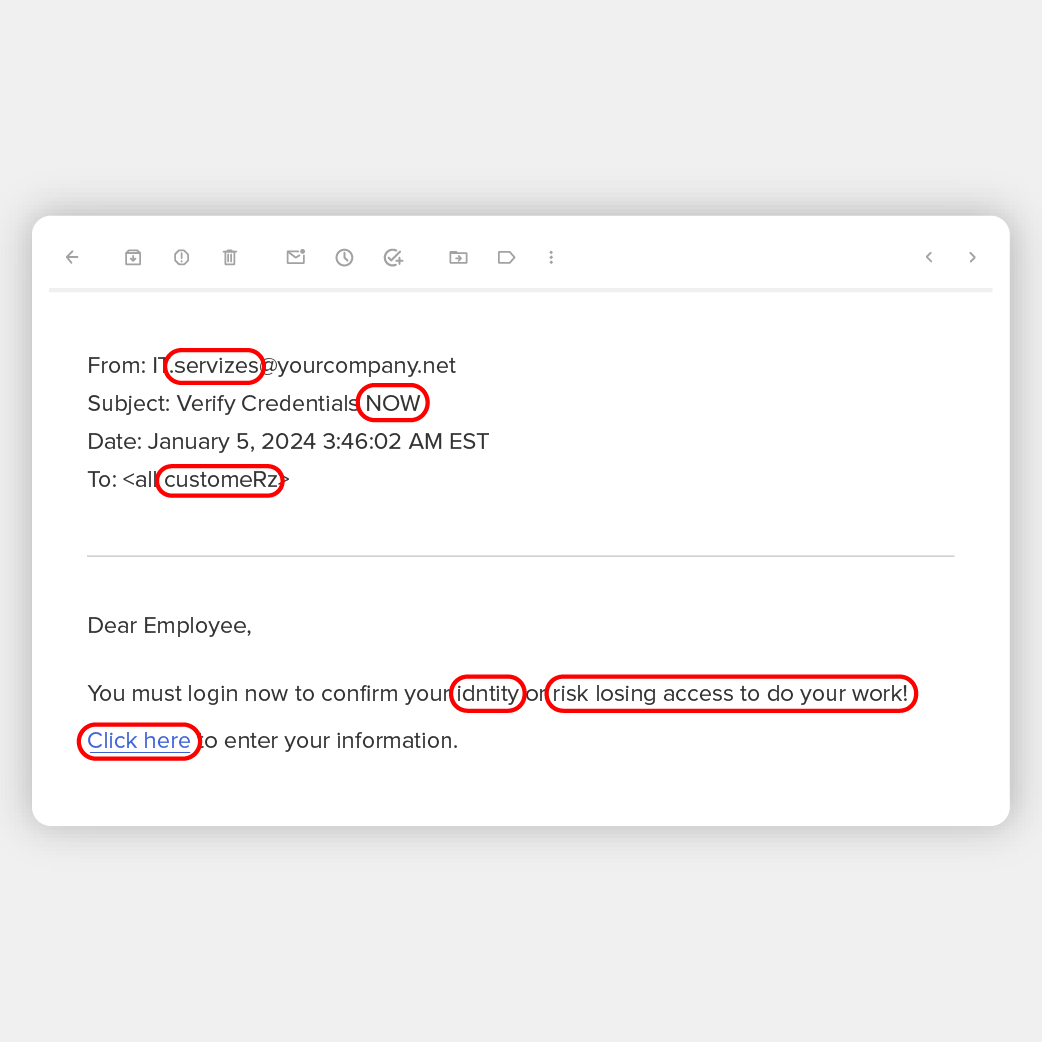
What’s phishing?
Phishing is principally a web based model of fishing – besides as a substitute of marine life, the objective is to draw customers of the gullible to reveal passwords and private info by clicking on a malicious hyperlink or opening an attachment. Typical assaults are despatched by e -mail.
Generally cyber criminals current as representatives of cloud service suppliers and ship them messages related to quite a lot of on-line providers and purposes.
Phishing messages are sometimes written skillfully. A basic tactic is to personalize dependable manufacturers akin to Fb and Microsoft, in addition to banks, Web service suppliers, the IRS and regulation enforcement companies. These emails comprise the suitable logos to look authorized. Anybody who follows their instructions and arms over their login particulars or clicks on a hyperlink is prone to be contaminated, discharge their gadget, obtain malware or closed out of their community and requested to pay a ransom.
As soon as they run into an software within the cloud, menace actors can increase their assaults on extra accounts and providers. For instance, violating a company’s Google or Microsoft Cloud offers the attacker entry to electronic mail accounts, contact lists and the creation of paperwork. By focusing on a phishing marketing campaign to acquire cloud proof, the unhealthy guys have a greater likelihood of attracting an even bigger payload.
How are you going to establish a phishing -E -mail or message?
Though phishing makes an attempt could seem genuine, there are clear indicators that point out {that a} message is a part of a phishing assault. Listed here are some to notice:
- Typographic or spelling errors.
- Uncommon use of symbols or punctuation.
- Content material is written incoherent or poorly.
- Message or electronic mail comes from an unknown recipient.
- Use generic greetings akin to ‘Expensive Buyer’ or ‘Expensive Consumer’.
- Normally discuss one thing that’s too good to be true.
- Have suspicious hyperlinks or file attachments.
What’s Spiesphishing?
Whereas Phishing is generalized by one phishing -E -mail being despatched to hundreds of thousands of individuals, Spiesphishing could be very focused. The aim is to jeopardize the credentials of a selected particular person, such because the CEO or CFO of an organization, as we reported in 2023.
In Spiesphishing, the messages are fastidiously produced. Criminals research social media placements and profiles to acquire as a lot info as potential a couple of sufferer. They will even entry the particular person’s electronic mail and stay invisible for months whereas evaluating the sort of site visitors the particular person is available in.
Spear -phishing messages are designed to be way more plausible than generic phishing makes an attempt as it’s primarily based on information taken from the particular person’s life and work. Exploration makes the Phishing -E -mail, textual content or mentions quite a lot of particular person.
Within the cloud, a goal with excessive worth could be somebody with administrative privileges for techniques that reach 1000’s of particular person accounts. By compromising one id, hackers have free rein to contaminate 1000’s of customers.
See: Safety of Linux coverage (TechRepublic Premium)
What’s the major distinction between phishing and spiesphishing?
What distinguishes Spiesphishing from abnormal phishing is that the message usually has way more particulars and accepts a tone of fame. The extent of shock and urgency is usually gained in spiesphishing and sometimes entails the switch of cash.
| Phishing | Spiesphishing | |
|---|---|---|
| Goal | Mass or giant group of individuals | Particular person or group with authority (CEO, CFO, IT directors) |
| Message’s stage of element | Low-to-medium | Very excessive |
| Tone of the message | Generic or basic | Depict familiarity with Goal; personalize |
| Timeframe | Finished in a single case | Finished over an extended time period |
| Depth of analysis required | Layer | Very excessive |
| Methodology/medium | Textual content, name, on-line message or e -mail | Are often performed by way of enterprise -e -E -mails |
| Finish -goal | Stealing a person’s credentials or buying small quantities of cash from the sufferer | This normally entails transferring giant quantities of cash or confidential information |
To be clear, most of the pink flags for potential Phishing -E -E -Poses additionally apply to Spiesphishing. It incorporates typos within the textual content, unhealthy grammar, electronic mail from unknown recipients, suspicious hyperlinks, a false sense of urgency or requests by e -mail to enter confidential info.
Phishing -E -POSSE goes to giant portions of individuals reasonably than to particular people. For instance, “NE -mail could be despatched to 1000’s of individuals or everybody in a single firm who tells them they need them to confirm their credentials by clicking on a hyperlink and getting into a kind.
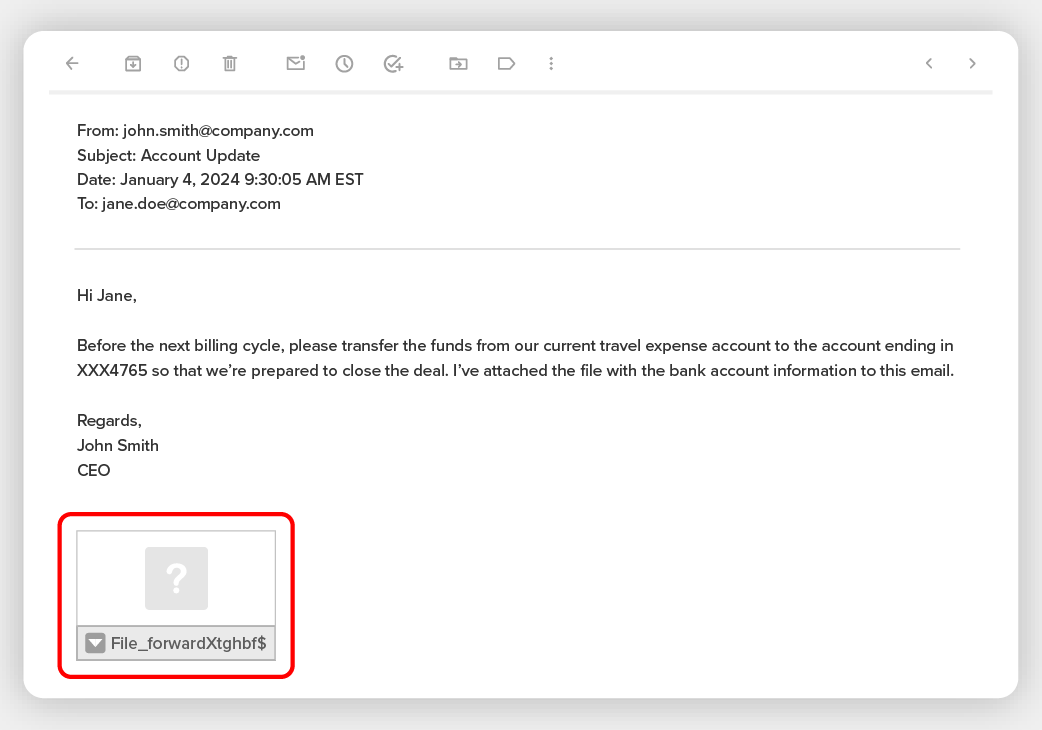
Spiesphishing is extra particular. For instance, the assistant of a CEO could be focused by a prison who personifies’ NE put up of the CEO. The hacker has been monitoring e -mail messages and social media for months and is aware of {that a} massive deal is about to go down at some extent the place the CEO is abroad and seals the settlement.
The prison then sends’ Ne put up that both seems just like the CEO, and even despatched among the CEO’s account, and tells the assistant that there was a change of plans and instantly $ x million to a brand new account transferred.
Find out how to defend your self from phishing and spiesphishing
There are totally different steps that organizations can take to guard themselves from phishing and spiesphishing assaults.
Set up an anti-spam filter
A spam filter will catch as much as 99% of the Spam and Phishing -E -E -mails. They don’t seem to be infallible. However they do catch quite a lot of it. Spam filters are consistently up to date primarily based on the newest scams and hacker methods, so do not go with out one.
Use a vpn
A VPN is a digital personal community that gives those that work remotely, larger privateness for messages than the Web. The person connects utilizing an encrypted tunnel, making it troublesome for another person to intercept the information. The usage of a VPN additionally makes it tougher for phishers to succeed by including extra low safety to e -mail messages and cloud use.
Leverage Multi-Issue Verification (MFA) Options
MFA should all the time be applied. If somebody jeopardizes a password, they will do no hurt as a result of it should be verified by permission from an authenticator app, a code despatched by textual content, a biometric or one other verification technique.
Set up antivirus software program
Antivirus software program was the unique safety safety that promised to forestall techniques from being contaminated by viruses. They did the job for some time. However hackers found out methods round them. Nonetheless, with out it, quite a lot of malware would trigger devastation within the enterprise. Be certain that antivirus software program is a part of your security arsenal because it catches every kind of viruses and malware.
Implementing Software program for Managing Cloud Safety
Cloud security place administration consistently screens cloud disaster by way of a mixture of prevention, detection, response and forecasting steps that handle the areas the place the danger could happen subsequent. This expertise provides a predictive method, which might make an enormous distinction in decreasing phishing and spiesphishing vendor.
This text was initially printed in February 2024. It was up to date by Luis Millares in January 2025.
(Tagstotranslate) Phishing
========================
AI, IT SOLUTIONS TECHTOKAI.NET
