The core goal of structured undertaking administration is to steadiness and steer a undertaking towards success amid a sea of unpredictable parts. Typically, undertaking execution goes easily, with clear timelines, sources, and minimal dangers. Nonetheless, as a rule, challenges come up that threaten to disrupt the undertaking’s stream. That’s the place a RAID log is available in to assist get issues again on monitor.
On this article, I’ll clarify what a RAID log is, learn how to use it, and its key advantages so you possibly can see why it’s such a useful device for undertaking administration.
1
monday.com
Workers per Firm Dimension
Micro (0-49), Small (50-249), Medium (250-999), Giant (1,000-4,999), Enterprise (5,000+)
Any Firm Dimension
Any Firm Dimension
Options
Agile Growth, Analytics / Reviews, API, and extra
2
Wrike
Workers per Firm Dimension
Micro (0-49), Small (50-249), Medium (250-999), Giant (1,000-4,999), Enterprise (5,000+)
Medium (250-999 Workers), Giant (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Medium, Giant, Enterprise
Options
Agile Growth, Analytics / Reviews, API, and extra
3
Cerri Mission
Workers per Firm Dimension
Micro (0-49), Small (50-249), Medium (250-999), Giant (1,000-4,999), Enterprise (5,000+)
Small (50-249 Workers), Medium (250-999 Workers), Giant (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Small, Medium, Giant, Enterprise
Options
Agile Growth, Analytics / Reviews, API, and extra
What’s a RAID log?
A RAID log is a undertaking administration device that paperwork and tracks points which will come up throughout a undertaking. The RAID log is created through the undertaking planning section and is a central doc the place undertaking dangers, assumptions, points, and dependencies are recorded.
All through the undertaking lifecycle, a RAID log is a reference level, permitting for higher communication, group, and problem-solving amongst staff members.
What does RAID stand for?
The acronym “RAID” stands for Dangers, Assumptions or Actions, Points and Dependencies or Selections. Notice that “A” and the “D” within the acronym have twin parts, that means they will confer with assumptions or actions, in addition to dependencies or selections, relying on how the RAID log is structured for a selected undertaking.
Dangers
In a RAID log, dangers are potential issues or uncertainties that might negatively affect the undertaking’s end result. They’re issues that may occur sooner or later, and figuring out them early helps in planning mitigation methods to keep away from or scale back their affect. Having a undertaking danger administration in place can assist be sure that the undertaking runs easily.
Efficient danger administration consists of figuring out, assessing, and prioritizing dangers and taking steps to manage or mitigate them. This proactive strategy minimizes disruptions, avoids expensive delays, and will increase the possibilities of undertaking success.
Assumptions or actions
The choice on which to make use of in your RAID log between assumptions or actions is dependent upon your staff construction. Whilst you can select to make use of both assumptions or actions individually, you may as well use them each collectively.
Assumptions
Assumptions are the components undertaking leaders consider to be true for the undertaking’s success however aren’t confirmed information. Nonetheless, they’re essential to create a undertaking plan. For example, assumptions may embrace the provision of sources at a selected time, stakeholder assist, and even particular deliverable expectations. Documenting assumptions helps preserve the staff conscious of those uncertainties and monitor them in the event that they end up in another way than anticipated.
Actions
In some RAID logs, “A” may additionally stand for Actions—particular duties or steps wanted to handle dangers, points, or dependencies. Take into account them duties the staff carries out to handle a danger, clear up a difficulty, or deal with a dependency. Actions are like a “to-do checklist” for the undertaking. Each often has an individual liable for it (proprietor) and a deadline, so everybody is aware of who’s dealing with what and by when.
For instance, if there’s a danger {that a} key useful resource won’t be out there, an motion could be to determine a backup particular person or useful resource prematurely. Or if there’s a difficulty with delayed supply, an motion could be to observe up with the seller to hurry issues up. Monitoring motion objects is useful as a result of it retains the staff accountable and clarifies who’s doing what to unravel any points.
Points
Points are identified issues that come up through the undertaking. Not like dangers, that are potential future challenges, points are present obstacles impacting undertaking progress. By documenting points as they come up, the undertaking staff can monitor them, assign sources to resolve them, and guarantee they’re managed on time to attenuate affect on the undertaking’s success.
Dependencies or selections
The “D” in RAID can also be a twin part—it might probably characterize dependencies or selections.
Dependencies
Dependencies are just like the connections between duties in a undertaking—they’re the “if this, then that” a part of the plan. Consider them because the steps that depend on one another to maneuver ahead. For instance, let’s say you’re constructing an app. You may’t begin testing the app till the event staff finishes constructing it. Right here, testing is dependent upon growth being finished first.
Dependencies are necessary to trace as a result of they present the place one delay can result in one other. When you understand the place your dependencies are, recognizing potential jams and planning round them is simpler.
One other instance may very well be in occasion planning. You may’t print invites till the occasion location and date are confirmed. Right here, printing is dependent upon the choice concerning the venue and timing. Understanding these dependencies means you possibly can keep away from surprises or last-minute rushes.
Selections
Selections in a RAID log are all of the necessary selections made through the undertaking that might affect how issues end up. These selections would possibly contain price range approvals, modifications to the undertaking scope, and even selecting one vendor over one other.
Documenting selections is useful as a result of it data the “who” and “why” behind sure selections. instance of a call could be deciding between two software program instruments for the undertaking. One device could also be cheaper, however the different is quicker and simpler to make use of. As soon as the choice is made, you possibly can log it together with the reasoning so everybody is aware of what went into that alternative.
RAID log advantages
RAID logs profit companies, undertaking managers, stakeholders, and undertaking groups, as they supply a structured option to monitor and deal with the numerous components that affect a undertaking’s end result.
- Mission management: The RAID log acts as an early warning system, serving to to determine potential roadblocks or challenges that might derail the undertaking if not resolved.
- Proactive danger identification and administration: A RAID log helps determine potential dangers early on, permitting the staff to take proactive measures to mitigate or keep away from them.
- Clear documentation of assumptions: Assumptions made on the outset of a undertaking be sure that all stakeholders clearly perceive what’s assumed to be true throughout undertaking execution.
- Correct challenge monitoring and determination: The RAID log offers a centralized place to trace points as they happen. By noting points, their homeowners, and determination progress, the RAID log makes assigning duty for challenge decision simpler and extra dependable.
- Mission postmortem evaluate: The RAID log offers a superb useful resource for retrospective critiques. The dangers, points, and selections made through the undertaking can assist inform future initiatives and determine areas for enchancment.
RAID log finest practices
To maximise the capabilities of a RAID log, it’s necessary to observe finest practices. Listed below are some important tips to stick to so your RAID log is a useful undertaking administration device.
Common updates all through undertaking lifecycle
Replace the RAID go browsing an everyday schedule to mirror the undertaking’s present state. For instance, chances are you’ll select to replace it weekly or after main undertaking milestones. If new dangers or points emerge, or if the standing of an current danger or challenge modifications, replace the log promptly.
Prioritize and categorize
Assign a precedence—Excessive, Medium, Low—to dangers, points, or dependencies primarily based on their potential affect and probability. Group dependencies into classes corresponding to inbound/outbound, technical/operational, or time-sensitive so the staff can give attention to essentially the most urgent ones.
Assign possession
Assign an individual or staff to handle every part. This creates accountability and ensures well timed motion. Embrace progress updates for every entry, exhibiting what actions have been taken, what’s been resolved, and what nonetheless requires consideration.
Use a easy and structured format
Use a constant format for all entries within the RAID log to make it straightforward to evaluate and replace. For instance, you possibly can use a desk format with columns like:
- ID
- Description
- Standing
- Affect
- Chance
- Proprietor
- Mitigation plan
- Due date
It’s also possible to leverage templates and undertaking administration software program to take care of the RAID log. Standard software program choices embrace Smartsheet, monday.com, ClickUp, and Jira.
Easy methods to create and use a RAID log
To make use of a RAID log, you possibly can create a easy desk or spreadsheet, with every column devoted to one of many 4 classes. Nonetheless, to make sure it’s useful for all events concerned within the undertaking, it’s paramount to centralize the log in a shared location the place the entire staff can entry and replace it in real-time.
Comply with the steps beneath to create your RAID log and use it to execute your undertaking.
- Select the format: Resolve on the platform you want to use. Some individuals desire spreadsheets, like Google Sheets or Microsoft Excel, because it’s the simplest possibility. It’s also possible to use undertaking administration software program like Notion, Asana, ClickUp, or Smartsheet.
- Create a RAID log template: Create a desk or spreadsheet with columns for every part—Dangers, Assumptions/Actions, Points, and Dependencies/Selections. Embrace different columns for particulars like description, precedence degree, assigned particular person, standing, and due date.
- Assign possession: Every merchandise within the RAID log ought to have a chosen proprietor. This staff member is liable for monitoring and updating its standing.
- Often replace the log: Replace the RAID log at common intervals—weekly, bi-weekly, or at key undertaking milestones. Preserving the log present ensures it stays an correct device for decision-making.
- Evaluation for classes discovered: After the undertaking wraps up, evaluate the RAID log to collect insights. That is useful for bettering future initiatives. Analyze what dangers had been most impactful, which points brought about the largest delays, and the way efficient selections and actions had been.
RAID log templates
There’s no one-design-fits-all for making a RAID log template in your undertaking. You may add and take away classes primarily based in your undertaking necessities. The figures beneath showcase a easy, easy-to-read desk to trace all RAID classes in a single place.
Smartsheet
This template has primary choices for monitoring RAID log data, together with columns for RAID class, description, affect, proprietor, and precedence. It’s a good selection for a easy undertaking with a comparatively small staff.
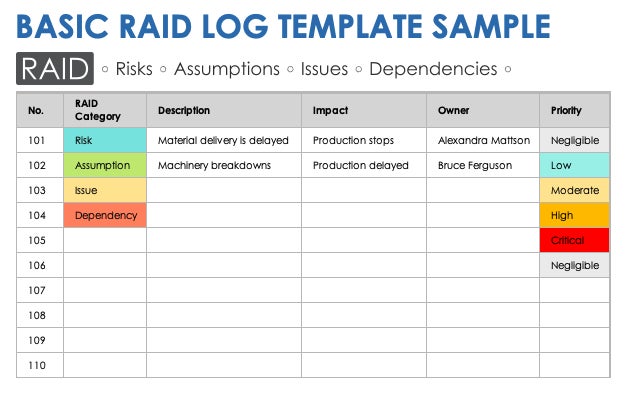
ClickUp
The ClickUp RAID log template is right for initiatives which have particular terminologies or staff buildings as a result of it affords a excessive degree of customization. You may customise the standing labels and the views and even add customized fields.
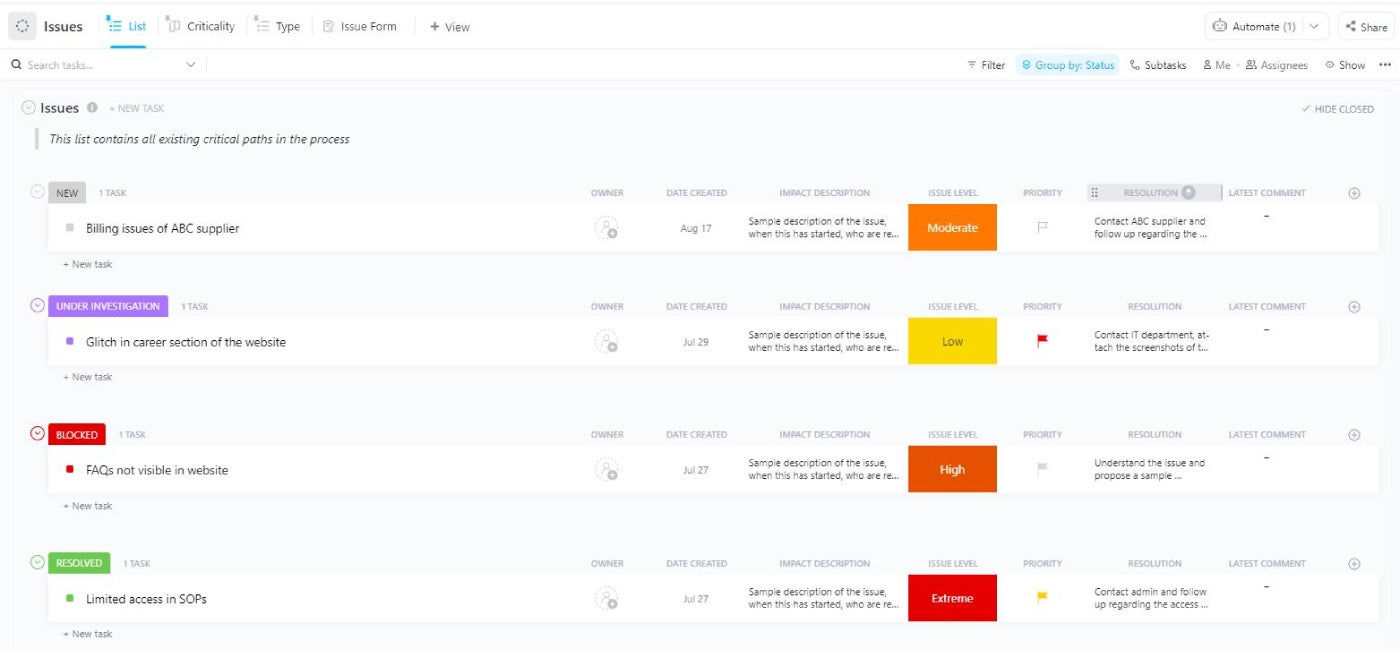
Google Sheets
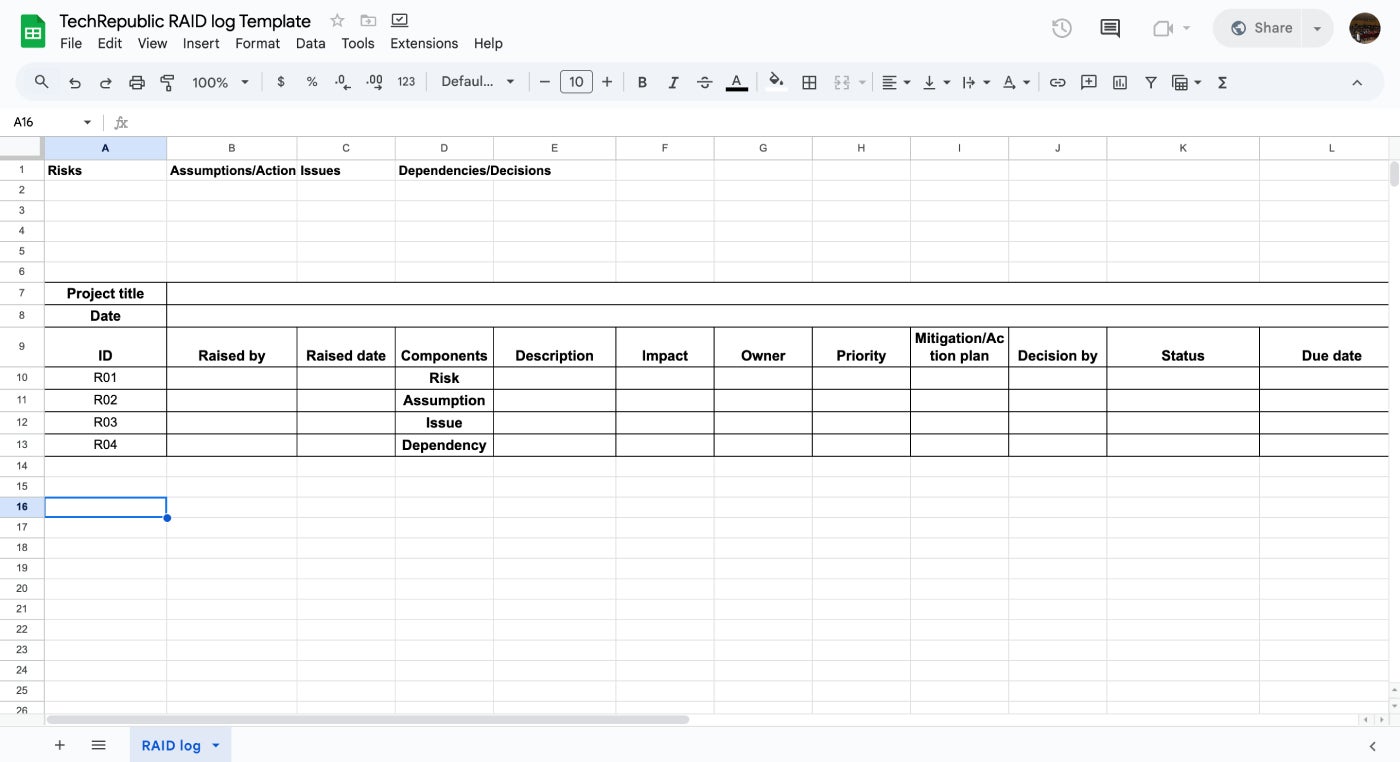
If you happen to’re not but utilizing devoted undertaking administration software program, I created an in depth RAID log template utilizing Google Sheets with additional columns for monitoring the chance and affect of dangers, plus detailed statuses. This template will be tailor-made to your undertaking’s wants and the extent of element you want for every RAID class.
Make a replica of the template to edit and use it free of charge in your undertaking administration.
For groups utilizing undertaking administration instruments like ClickUp, Asana, or Smartsheet, a RAID log will be arrange with filtered views, tags, and reminders. Create columns just like these above and use tags to mark every merchandise’s standing—as an example, “Excessive Precedence” for dangers or “In Progress” for points.
FAQs
What’s the distinction between a RAID log and a danger log?
A RAID log offers a structured strategy for managing dangers, assumptions, points, and dependencies in initiatives. Conversely, a danger log scope is slender, because it focuses solely on dangers, particularly figuring out potential occasions that might negatively have an effect on the undertaking. It particulars the affect, probability, proprietor, and mitigation plan for every recognized danger.
What’s RAID in agile undertaking administration?
In agile undertaking administration, the RAID framework can nonetheless be helpful, although it could be tailored barely to suit agile’s iterative, versatile strategy. Whereas RAID will not be a core agile device, it’s nonetheless helpful to doc and handle these parts, particularly in agile initiatives with bigger groups or complicated dependencies.
How do RAID logs work?
A RAID log works by documenting, monitoring, and managing 4 key parts that may considerably affect the end result of a undertaking: Dangers, Assumptions, Points, and Dependencies.
========================
AI, IT SOLUTIONS TECHTOKAI.NET
